mirror of
https://github.com/dongdigua/dongdigua.github.io
synced 2024-11-24 04:03:11 +08:00
1.6 KiB
1.6 KiB
Binary Exploit Resources I Recently Trying to Learn
resources
tools
notes on video
0x04: asm basics
to show assembly in the source code window in gud, M-x gdb-display-disassembly-buffer
0x06: tools
simple tools
hexdump
strings
all printable letters
objdump
disassembler
strace/ltrace
trace sys/lib call
0x0A: deal with numbers
endian?
tools
python
>>> int('111', 2)
7
>>> hex(123)
'0x7b'
>>> import struct
# https://docs.python.org/3.10/library/struct.html#format-characters
>>> struct.pack("<I", 0x61626364) # little endian
b'dcba'
>>> struct.pack(">I", 0x61626364) # big endian
b'abcd'iex
iex(1)> <<0x61626364::32>>
"abcd"
iex(2)> Base.decode16("61626364")
{:ok, "abcd"}
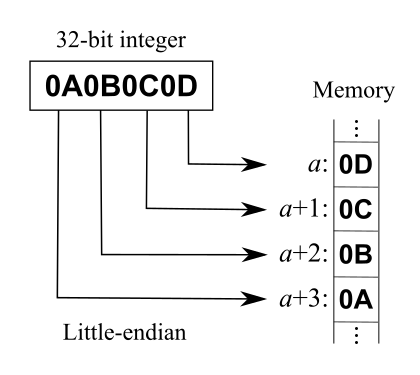 x86 is little endian
x86 is little endian